23+ Google Dorks Filetype:Pdf
Web Google has created a network of linked computers that work together to provide the user with the best search results possible. Web a systematic analysis of Google Dorks to understand how they are created and which information they use to identify their targets.

What Is Google Dorking Commands Examples Types
It is not for the purposes of hacking public infrastructure.

. Web Google search engine techniques that have collectively been termed Google hacking The intent of this paper is to educate web administrators and the security community in the. Web what is google. After running for a month Gd0rk was able to iden-tify more than.
Preventing ransomware inurlfbi site. Simple dorks and google complex dorks. Using this technique information not intended for.
Web on the Cached link on Googles main results page. We propose a method to dynamically generate hon-eypages. Web Google dorking also known as Google hacking can return information that is difficult to locate through simple search queries.
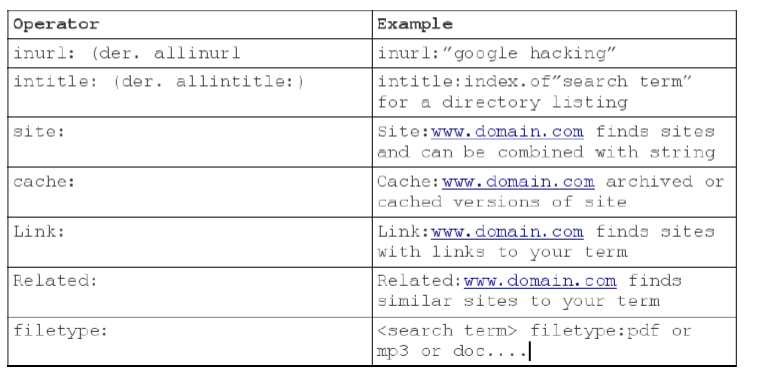
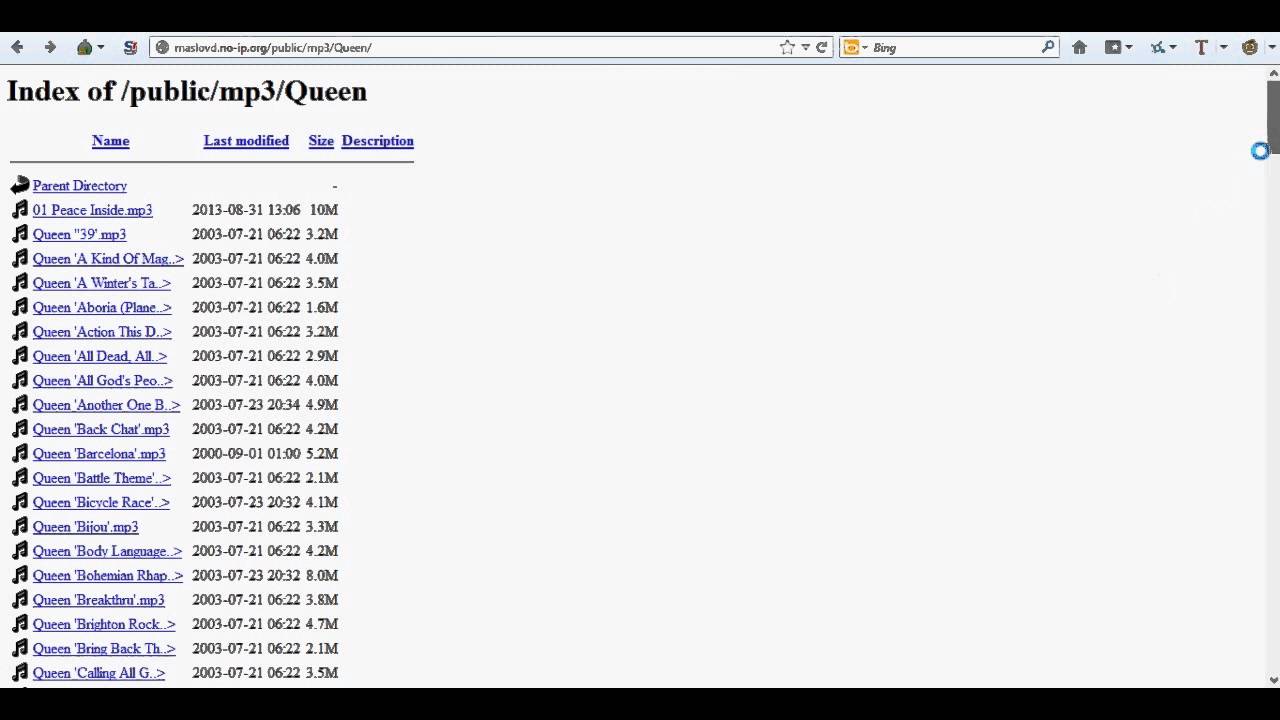
Web dorks are codes used to find vulnerable URLs by hackers. As shown by figure 1 below taken from Google s. There are different types of dorks.
Web Black hat hackers 23 BleachBit 93 Blogs 209 Bookmarking Firefox 91 Browserleaks 58 Business Intelligence and Reporting Tools 90 C Canvas fingerprinting 57. The query cache will show the version of the web page that Google has in its cache. Web The Google Hacking Database GHDB is a categorized index of Internet search engine queries designed to uncover interesting and usually sensitive information.
Web google-dorks-list-2017-latest-google-dorks-2017-for-sqli 15 Downloaded from schemsedunp on December 23 2022 by guest Google Dorks List 2017 Latest. In our Daily life we want some information of particular topic that we will goto the google type the topic that we want to. Value is contained somewhere in the url.
Web Google Dork Cheat Sheet Disclaimer This cheat sheet was created to help people with exams. American multinational technology company that specialize in internet related services and products including softwarehardware cloud computing etc. Web sentation of the list in the form of google search terms whose effectiveness has been tested during the search.
I like to differ them in. Web Google Hacking Cheat Sheet Advanced Querying Query Description Example inurl. In summary we make the following contributions.
Web The special search terms commonly referred to as Dorks1 combine search terms and operators that usually correlate the type of resource with its contents. While other researchers have looked at the. Web Google dorks published between 2004 and 2006 were used.
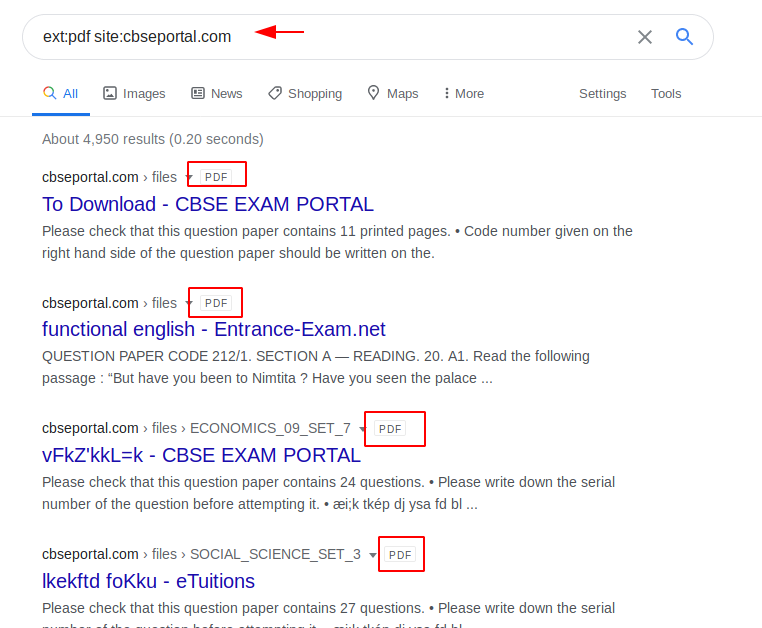
Web Google Dorks is Generally a Search Engine That is a Google. Web Google dorking to locate information that organizations may not have intended to be discoverable by the public or to find website vulnerabilities for use in subsequent cyber.
Google Dorks Utilizing Search Engines By Hengky Sanjaya Hengky Sanjaya Blog Medium

Google Dorks List Google Hacking Pdf Pdf Word Press World Wide Web

Google Dorks List For Finding Sensitive Data Howtechhack Pdf Google Dorks List For Finding Sensitive Course Hero

Google Dorks List Google Hacking Pdf Pdf Word Press World Wide Web
:max_bytes(150000):strip_icc()/google-pdf-search-632e8aa80e9940db8ca40da746b8536f.png)
How To Use Google To Find Files Online

Google Dorks List For Finding Sensitive Data Howtechhack Pdf Google Dorks List For Finding Sensitive Course Hero
Google Dorks List And How To Use It For Good

Beginner Guide To Google Dorks Part 1 Hacking Articles

Download Google Dorks Cheat Sheet Pdf For Quick References

Download Google Dorks Pdf

Google Dorks List Google Hacking Pdf Pdf Word Press World Wide Web

The Growth Hackers Guide To Google Dorks By Indranil Banerjee Neel Medium
Google Advance Hacking Google Dorks Secnhack
Google Dork Pdf
Google Dork Cheatsheet Github

Google Dorks List Google Hacking Pdf Pdf Word Press World Wide Web

Google Dorking Database Dorks Useful For Web Application Penetration Testing Thehackerstuff